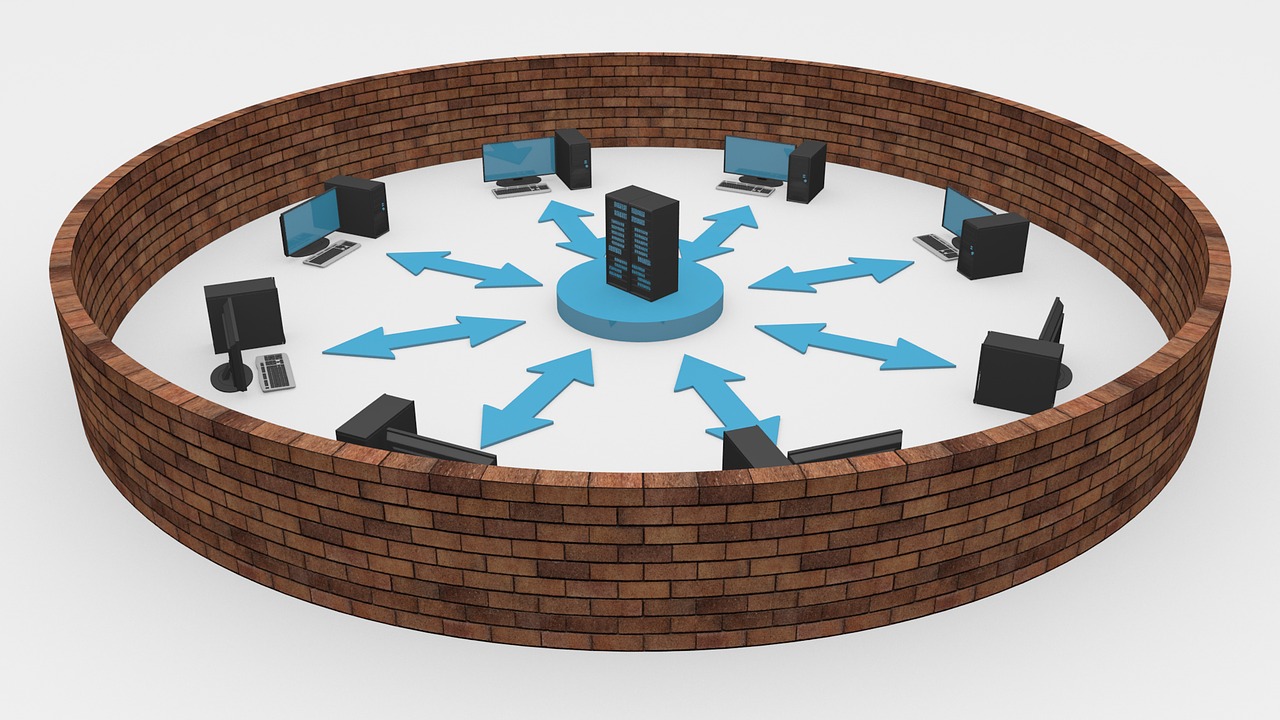
Multiple wireless router chipsets were discovered to be vulnerable to authentication bypass, giving a threat actor control of network traffic passing through the affected device(s). A successful attack occurs when an attacker injects arbitrary (unencrypted) packets into networks with WPA2 protection. Upon injection, the packets are considered to be legitimately routed traffic and encrypted responses are received.
This attack is especially dangerous because the attacker doesn’t require any knowledge of the pre-negotiated key used in the network encryption. In addition to controlling traffic on a network, the attacker can determine whether their packets successfully reach an active system.
The following chipsets were identified to be at risk:
Patches for devices including the chipset are available for Mediatek and Realtek and must be requested from the respective manufacturers. However, Qualcomm (Atheros) has issued a statement saying they have discontinued the affected chipsets and have verified that their currently supported chipsets are not affected by the vulnerability. Those using the identified chipset and firmware versions are encouraged to upgrade as soon as possible or replace vulnerable access points (especially in the case of the obsolete Qualcomm devices).
Source: Security Boulevard
Introducing ISO 42001 – the world’s first international management system standard focused specifically on AI.…
Data breaches and cyberattacks have become daily concerns for information security professionals and business leaders.…
It is an undeniable fact that all applications and infrastructures are essentially in need of…