
Businessman touching tablet and laptop, managing global structure networking and data exchanges customer connection on workplace. Business technology and digital marketing network concept.
Let us begin by describing how to approach Cyber Supply Chain Risk Management (C-SCRM) and the risks your vendors pose to you. Then we will discuss if you should require them to show evidence that penetration testing was conducted and what remediations were taken.
For simplicity let us split suppliers into three tiers: Tier 1, Tier 2, and Tier 3. We can use the following parameters to construct a function to determine where they fit: volume and sensitivity of data they hold on our organisation, the connectivity they have to our networks and compliance requirements.
Then we need to discover the cyber posture of these vendors (Are they ISO compliant? Do they regularly get tested? Are they Cyber Essentials certified?), and depending on which tier they fit in, we will come up with a risk rating for that supplier. A risk matrix could look as follows.

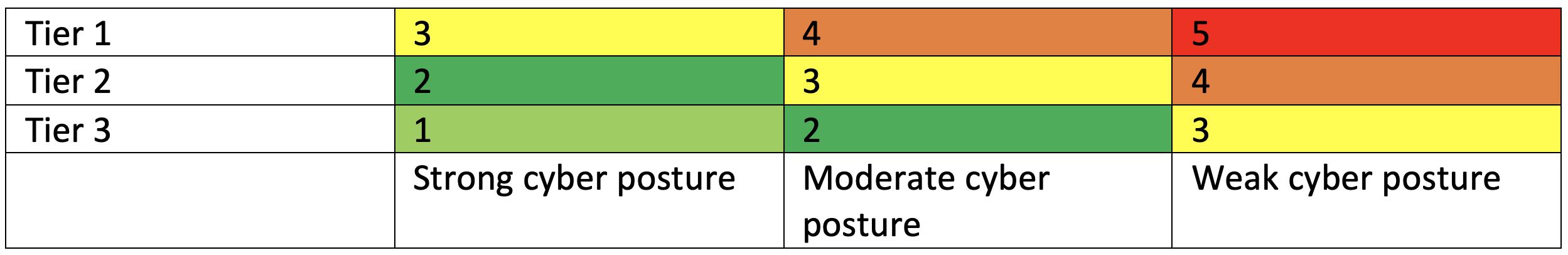
As an organisation, let us assume we would only accept a cyber risk score of 3 or below for our suppliers. This would mean that for Tier 3 suppliers, we would not even bother to measure their cyber posture as it would be an unnecessary time investment. For Tier 2 suppliers, we would need to ensure that they follow a moderate security posture (i.e maybe Cyber Essentials certified?). And finally, for the Tier 1 suppliers, we would need to verify that they take cyber security very seriously.
As a result, it is important to note that our organisations would prefer having lower Tier suppliers wherever possible, therefore as an example, only provide them with the connectivity they absolutely require.
Your vendors may provide you with products that are within your corporate networks, design and/or host web applications for you, or they might be delivering a larger managed service. From an attacker’s perspective compromising these hosts/applications, would be considered acquiring a foothold within your estate. These tend to be your Tier 1 suppliers as a result, they should be scrutinised in greater detail.
A trend is appearing, to “island hop” from a MSPs to target networks. Island hopping involves targeting a trusted relationship you have (a vendor, a partner, a client etc…) to gain the initial foothold on your network (i.e abusing the trust relationship). This happens more often than you would think, indeed, according to Carbon Black “half of cyber-attacks today leverage island hopping.” This approach is not new, indeed Chinese threat actors were responsible for a large campaign targeting MSPs beginning in late 2016. And recently, the SolarWinds hack has brought this risk to mainstream news (albeit poorly explained).
This is a difficult question to answer, and it depends on the risk level of your suppliers and what type of service/product they provide you, but below are two points to keep in mind:
Risk Crew offers a scalable solution that is fully customisable to meet your specific risk objectives. It can be designed and deployed within your existing business’ supplier management processes or platforms or automated and fully outsourced to Risk Crew for management.
Introducing ISO 42001 – the world’s first international management system standard focused specifically on AI.…
Data breaches and cyberattacks have become daily concerns for information security professionals and business leaders.…
It is an undeniable fact that all applications and infrastructures are essentially in need of…