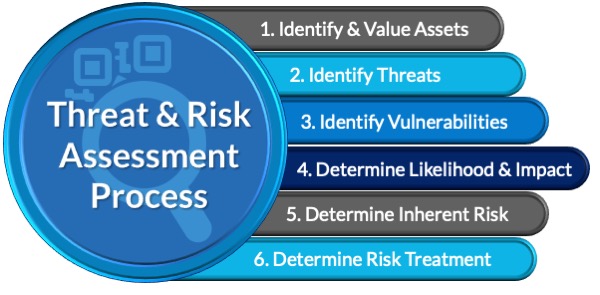
The only constant in cyber security is “change”. Markets change. Businesses change. Staff change. Information assets change. Technology changes. Vulnerabilities change. Threats change.
Everything changes. These constant changes require a continual reassessment of your risk environment. Your best tool to do this is conducting information security threat and risk assessments.
Industry best practices and most compliance frameworks dictate that they should be conducted annually or following any significant changes to the systems used to process, store or transmit your business’ information assets. This may be logical, however, few businesses invest in this fundamental practice and so fail to protect their business from the ever-changing threat landscape. We have designed a straightforward, cost-effective service for providing this fundamental requirement.