What is Risk-Driven Application Security Testing?
Attackers play the game on an application-level – so should you. Risk-Driven Application Security Testing Service is designed to ensure the security integrity of your business-critical applications before launch. This innovative service is founded on the principle of security by design and is comprised of four critical activities: first identifying the applications’ design flaws, then risks to the assets it processes followed by identifying its attack surface and then customising a security penetration test based on the flaws, risks and attack vectors specifically associated with the application.
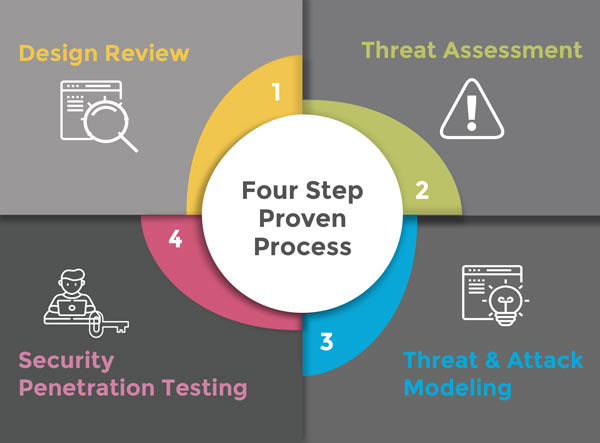
This holistic approach results in a more robust and applicable security posture for the applications that process store and transmit your business-critical information assets. It confirms that they are ‘fit for purpose’ and significantly reduces the risk of a breach.














