What is Red Team Testing?
Red Team Testing seeks to test all of the security controls you have implemented across your business in your people, process, and technology against real-life cyber-attack methodologies based on open-source available information.
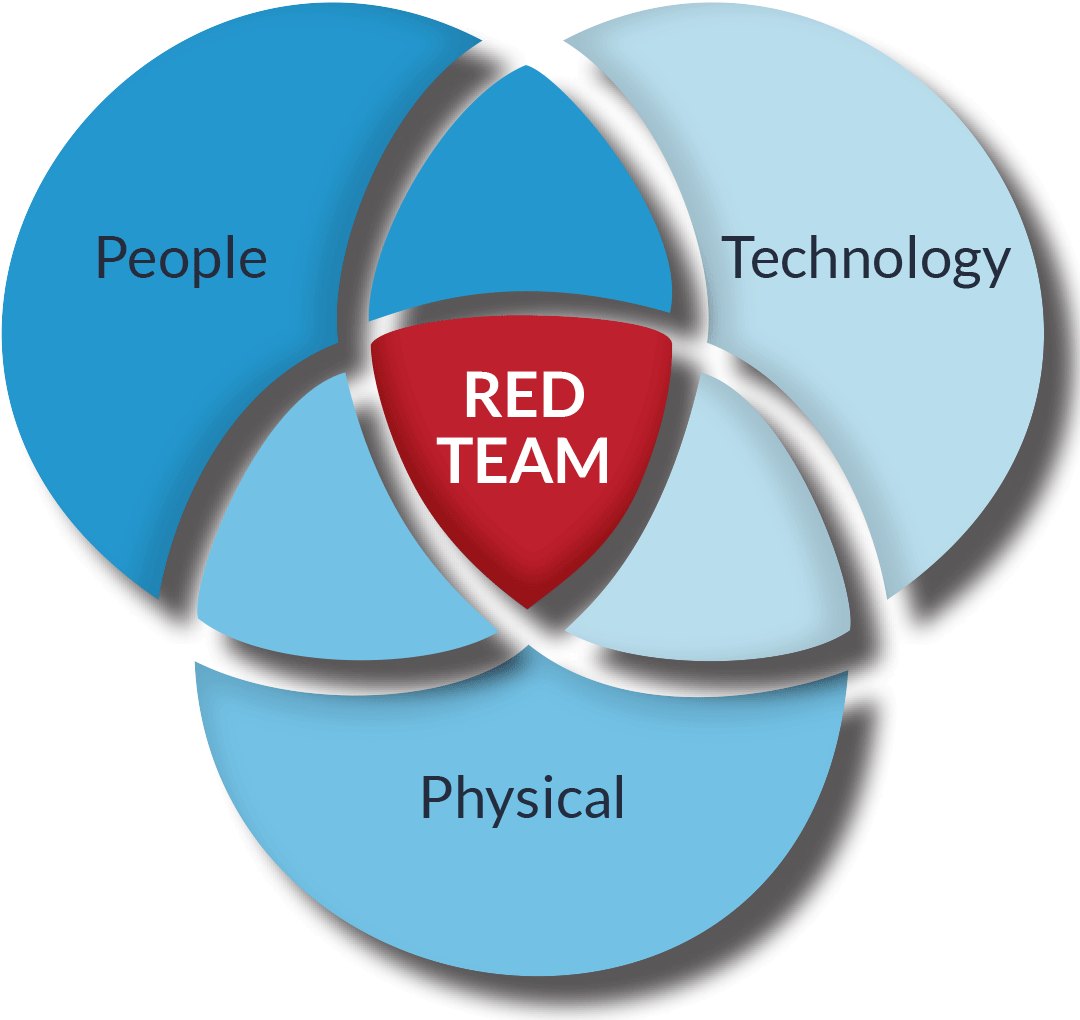
This holistic, intelligence-led testing approach differs from conventional security penetration testing, which seeks to assess the security controls deployed in the systems that host your sensitive data. It’s an effective methodology for testing the organisation’s exposure and not just its technology.
The driving principle of conducting a Red Team Test is: “Know thyself”. This testing has a proven methodology for understanding how well your organisation would fare against a real-life cyber attack.
Let Risk Crew design and deliver a systematic Red Team Test to holistically test the security controls in all the pathways to your sensitive data and achieve the best return on investment for your cyber security testing budget.
You don’t know what you don’t know – until you test what you think you know.


