In this post, you’ll learn why vishing is successful and what you can do to mitigate the risk of being vished. Vishing is a form of social engineering. Much like phishing, it can be used to manipulate people into giving away usernames, passwords and sometimes bank details. Vishing: Exploitation by voice commands Vishing is the […]
Good news. Bad news. The bad news is that cyber security threats to businesses are increasing exponentially every day. But then, you already knew that. The good news is that the best defence against these ever-growing threats is already at work in your business – your staff. In 2019, 60% of the breaches that occurred […]
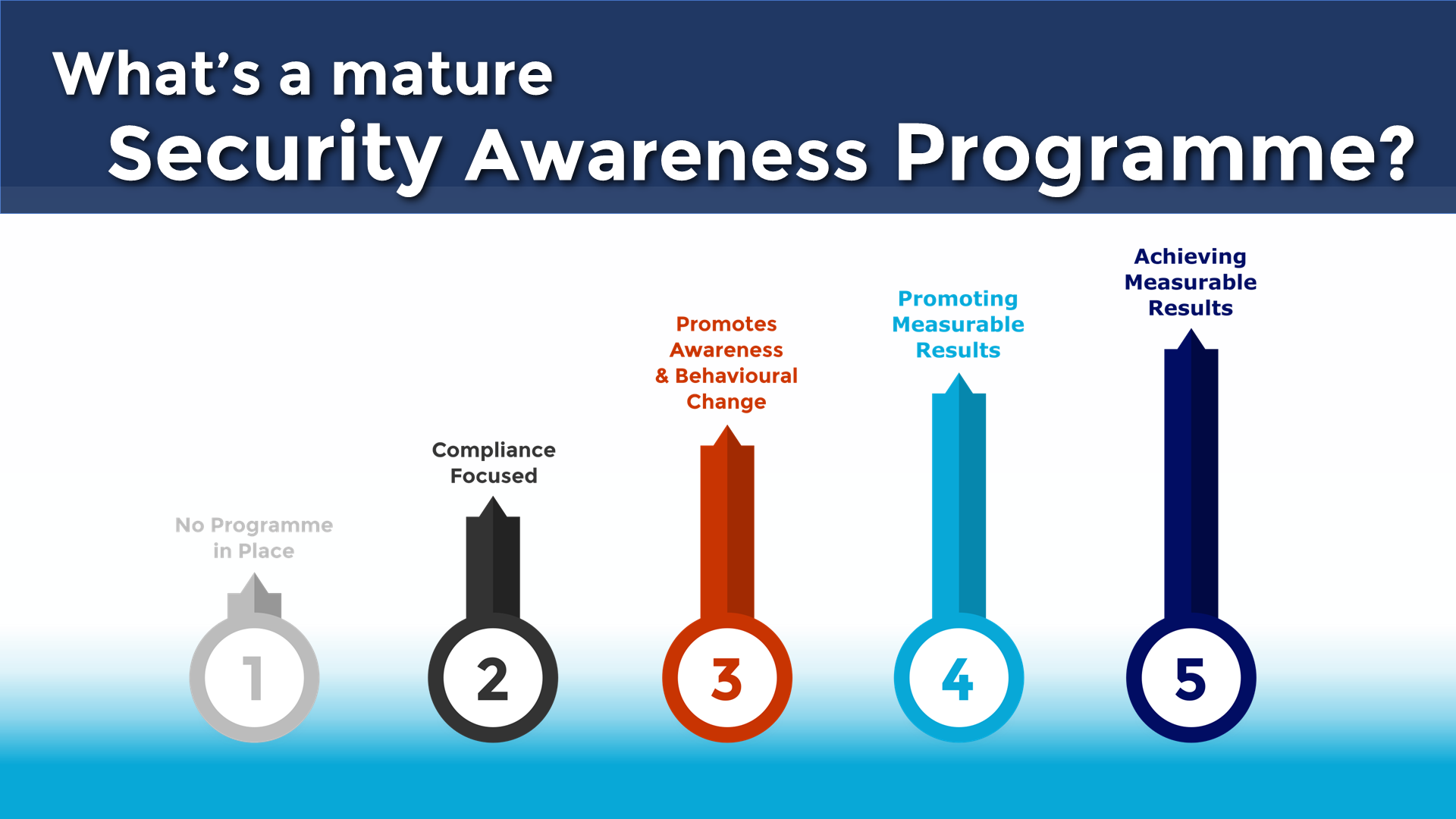
Good information security awareness training can turn your workforce into the strongest line of defence instead of the ‘weakest link’. Around 70 – 80% of all breaches can be attributed to the human element, yet companies often focus their resource of software-based security solutions. Where do we start? If you haven’t already found our post […]