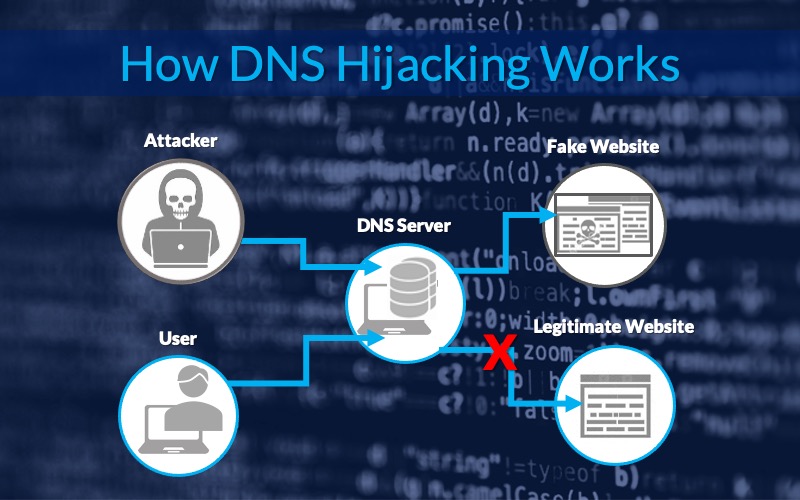
The term Domain Name System (DNS) hijacking unfortunately tends to be misused in the industry, which includes DNS poisoning for instance. In this blog post we will use the definition adopted by the UK National Cyber Security Centre (NCSC) that states “DNS hijacking refers to the unauthorised alteration of DNS entries in a zone file on an authoritative DNS server, or the modification of domain configurations in relation to a domain registrar, by an attacker.”
Let us dissect this definition and focus on “modification of domain configurations in relation to a domain registrar” since this is the most common approach used by malicious actors.
DNS fundamentals
On the internet, we access resources such as websites with a domain name. This allows people to remember websites they are visiting. It is easier to keep track of youtube.com, bbc.com and facebook.com than all their IP addresses (which may change over time or might include many). Therefore, we need a mapping between IP addresses and domain names, which is the problem DNS addresses. However, it goes well beyond simply websites, for instance when you email someone at the BBC how does it know where that email should go? DNS again!
The ways in which it accomplishes this is beyond the discussion in this blog post, but you may have heard of GoDaddy or 123-reg.co.uk. These are called domain registrars where you buy your domain names. These companies work with the registries (in the UK, Nominet) to assign these domain names to you! Once you own a domain name you can point it to your website (DNS A Records) and to your email server (DNS MX records) from your account on a domain registrar.
Domain hijacking
In non-technical terms (given that it would be possible to get valid Transport Layer Security (TLS) certificates to that domain by using DNS TXT records), if an attacker has access to your account on a domain registrar, he/she could:
- Point your website to a malicious one where the end users would be oblivious to this (entering their credentials etc…) and then relay that information to the legitimate website.
- Point your email server domain to their IP address and therefore read all emails going to your organisation. The attacker could also send emails on your behalf.
Mitigations
It is therefore vital to protect these accounts on your domain registrar by:
- Enforcing strong passwords
- Utilising two-factor authentication
Furthermore, given that these records are in the public domain, they can be monitored for any changes (similarly it is possible to monitor any new TLS certificates signed on your behalf, this can be achieved through Certificate Transparency).
Finally, logs of the website and email server would indicate that the source IP addresses of all requests are the same if such an intercepting attack (man-in-the-middle) is taking place.