The DarkSide Ransomware Group is one of the many gangs that continue to rebrand themselves while expanding to gain more intelligence in 2022. So, is there any way to outsmart these groups? It almost seems like a losing battle. However, a strong defence can be created within your organisation, but first, it’s important to start with understanding how your attacker operates. From there, you can ensure you are implementing a security framework that encompasses technology, people and processes to defend and protect your business-critical information assets.
What is DarkSide ransomware?
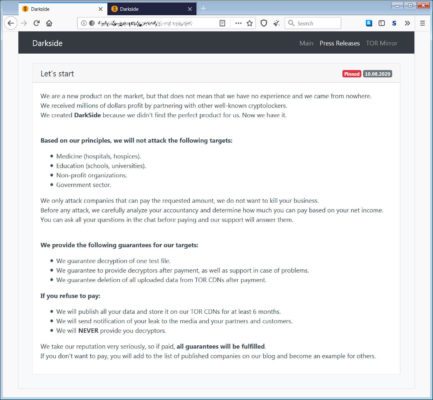
The DarkSide first showed up on the hacking battlefield in 2020 comprised of developers and affiliates that deploy ransomware. The DarkSide offers ransomware-as-a-service, RaaS platform, for “approved” affiliates, or rather cybercriminals, to deploy ransomware to infect organisations and then send a ransom note to negotiate payment with victims. DarkSide claimed they have an ethical backing that forbids their affiliates from deploying ransomware on critical and vulnerable organisations in industries including healthcare, education, the public sector and non-profits. But can you really trust cybercriminals to have an ethical or moral code and follow it? Especially when this group has rebranded itself three times…from calling themselves DarkSide, then BlackMatter and now Alphv (AKA: BlackCat).
How does Ransomware-as-a-Service work?
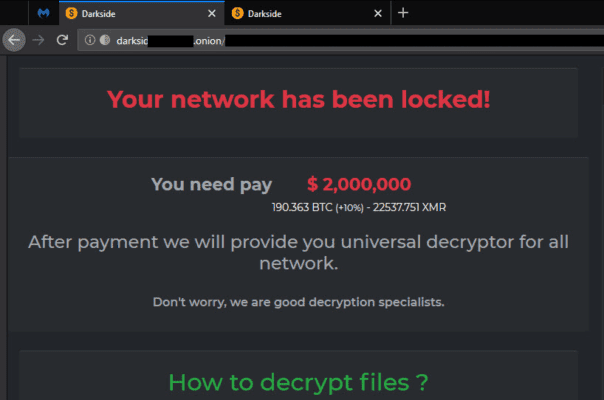
Attackers will gain access to an organisation’s network through techniques like phishing, accessing remote accounts, or through brute force attacks to then encrypt and take sensitive data. Next security protections are disabled, and any shadow copies are deleted to prevent users from recovering their encrypted data. Finally, the ransom note is delivered to inform the victim they’ve been hit and how they can pay the ransom by a specific time.
Who are the victims of DarkSide ransomware?
The most notorious attack carried out by the DarkSide group was the Colonial Pipeline Company attack, in 2021. The ransomware attack forced the company to take its systems offline for six days, which disrupted the fuel supply chain. This sent fuel prices to soar — as the pipeline accounts for 45% of the supply to the US east coast. Instantly this incident hit the FBI’s radar and was assumed to be a national infrastructure attack. However, on DarkSide’s blog, the group responded with the statement, “Our goal is to make money, and not create problems for society.” They go on to say they are apolitical and simply look to gain revenue from targets that have the financial backing to pay out large ransoms — commonly known as ‘big game hunting’.
Why should you care about DarkSide ransomware?
You should be aware of the DarkSide group and the other multiple ransomware gangs currently on the battlefield. 2022 predictions show that smaller gangs will push to survive by forming larger cartels as well as bringing on affiliates as the DarkSide does. Therefore, they become more well-funded and have better means to incorporate technology and deploy innovative business models into their operations to advance tactics and malware.
How to outsmart threat actors
At Risk Crew, we prefer to look at the brighter side of things. While no one can (as of yet) can stop these threat actors, there are several actions your organisation can take to strengthen your defence against attacks — some of which you most likely have in place.
Boost your defence and prevent ransomware incidents by:
- Educate end-users on how to identify malicious emails
- Perform social engineering simulated attacks that include phishing and spearphishing
- Confirm user accounts have strong passwords that are changed regularly and do not use password managers
- Ensure multi-factor authentication is enabled on all user accounts
- Update operating systems, software and firmware on IT network assets
- Consider using a centralised patch management system
- Limit admin privileges to only those who need them
- Ensure robust network segregation and segmentation are in places to limit access to resources on the network
- Back up your data to a source, that is not connected to a network
- Prevent unauthorised execution by disabling macro scripts from Microsoft Office files transferred via email and implementing application allowlisting
- Monitor outbound network traffic that would indicate data exfiltration
- Conduct security testing to discover vulnerabilities within your network
This is not an exhaustive list but having these security controls in place is a good start. Andy Whitaker, the Senior GRC consultant at Risk Crew, says in order to have a strong defence, it’s vital to imbed a holistic security approach that links technology, people and processes. Missing just one of these links could lead to vulnerabilities and open your systems up to attacks.
Now that you have a good understanding of what DarkSide ransomware is, how it works and where it’s going, you can begin strengthening your defences against all gangs and cartels. Even if you already have a good framework in place, you should consider conducting a Ransomware Audit. An audit can provide an unbiased assessment of your processes, technology and your staff’s ability to effectively identify and quickly respond to attacks.
Get ransomware ready
The Crew is always happy to help get organisations Ransomware ready. For those that are just starting to build defences, we’ve created the Ransomware Readiness Playbook that provides an in-depth understanding of attacks and the cybercriminals behind them. Plus, it comes with a readiness and response checklist to help you understand your strengths and weaknesses to improve upon. If you have a mature cyber security framework in place, we offer a Ransomware Readiness Audit service that uses a real-world attack testing methodology for assessing your vulnerability to ransomware.