Risk Rating: CRITICAL
Affected Products: MOVEit Transfer
Affected Version: 2023.0.0 (15.0), 2022.1.x (14.1), 2022.0.x (14.0), 2021.1.x (13.1), 2021.0.x (13.0), 2020.1.x (12.1)
Patched Version: CVE-2023-34362, CVE-2023-35036
Proof-of-Concepts available: no
Vendor: Progress Software Corporation
Date: 31/05/2023, 09/06/2023
Introduction:
A severe Zero-Day vulnerability was disclosed, which posed a significant risk to Progress MOVEit File Transfer software users. “Progress” has received and confirmed the reports indicating the potential exploitation of a SQL injection vulnerability in the MOVEit Transfer web application that could allow an unauthenticated attacker to gain access to MOVEit Transfer’s database in real-world scenarios. Consequently, it is of utmost importance for any organisation utilising MOVEit Transfer to take immediate action. It is critical to note that all versions of this widely used file transfer software are susceptible to this vulnerability.
Startling reports reveal that the infamous Cl0p ransomware group has initiated a series of targeted campaigns, compromising more than 20 organisations. These affected entities span critical sectors, including those Aviation, Transportation & Logistics, Entertainment, Financial Services & Insurance, Healthcare and Pharmaceuticals & Biotechnology. Notably, even Managed Security Service Providers (MSSPs) and Managed Information Technology Service Providers (MSPs) have not been spared from the clutches of this vulnerability.
Impact:
The CVE-2023-34362 vulnerability found in the MOVEit Transfer web application could allow an unauthenticated attacker to access MOVEit Transfer’s database. Depending on the database engine being used (MySQL, Microsoft SQL Server or Azure SQL), an attacker may be able to infer information about the structure and contents of the database and execute SQL statements that alter or delete database elements.
CVSS BASE SCORE: 9.8
Technical Analysis:
The identified vulnerability is leveraged in an attack chain to facilitate an arbitrary file upload through the moveitsvc service account, targeting the server’s \MOVEitTransfer\wwwroot\ directory. To execute this attack, the system’s svchost.exe process initiates the launch of w3wp.exe, an Internet Information Service (IIS) worker process. Subsequently, multiple files are written to a newly created working directory within the Temp directory.
It is important to note that the working directory and the subsequent files follow an 8-character pseudo-random naming convention. As an illustration, one instance of this attack resulted in the creation of the following files.
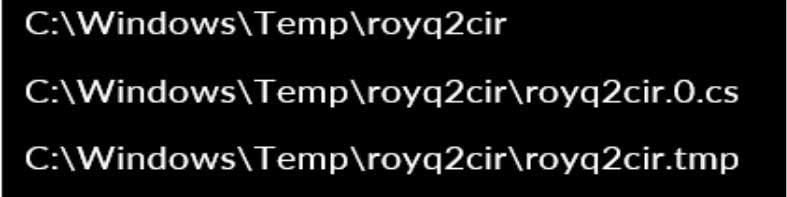
The w3wp.exe process launches csc.exe to compile the C# code into the payload, which is saved as human2.aspx.
Attack Vector:
In order to exfiltrate files, the attackers utilise the vulnerability by specifying the targeted File ID and Folder ID within the HTTP headers of a request directed towards the web shell. Subsequently, the web shell responds by providing the content of the specified file as a Gzip object in the server’s HTTP response. Notably, as a persistence mechanism, the attacker removes the pre-existing user account named “Health Check Service” and replaces it with a newly created user bearing the same username.
Affected Versions and Fixes:
MOVEit Transfer 2023.0.0: fixed in 2023.0.1
MOVEit Transfer 2022.1.x: fixed in 2022.1.5
MOVEit Transfer 2022.0.x: fixed in 2022.0.4
MOVEit Transfer 2021.1.x: fixed in 2021.1.4
MOVEit Transfer 2021.0.x: fixed in 2021.0.6
Remediation(s):
- Disable all HTTP and HTTPS traffic to your MOVEit Transfer environment. More specifically, modify firewall rules to deny HTTP and HTTPS traffic to MOVEit Transfer on ports 80 and 443 until the patch can be applied.
- Delete any instances of the human2.aspx (or any files with human2 prefix) and. cmdline script files.
- Apply patches.
Links & Resources:
- https://community.progress.com/s/article/MOVEit-Transfer-Critical-Vulnerability-31May2023
- https://nvd.nist.gov/vuln/detail/CVE-2023-34362
