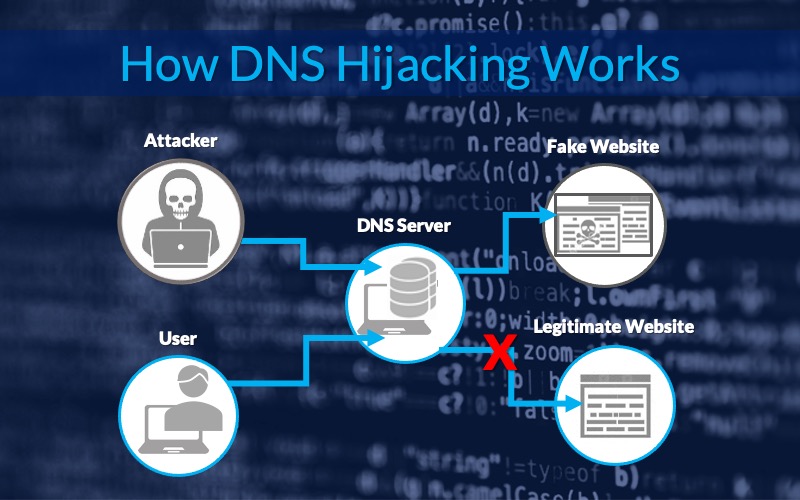
The term Domain Name System (DNS) hijacking unfortunately tends to be misused in the industry, which includes DNS poisoning for instance. In this blog post we will use the definition adopted by the UK National Cyber Security Centre (NCSC) that states “DNS hijacking refers to the unauthorised alteration of DNS entries in a zone file […]
The Windows utility developer IObit forums hacked over the weekend, for the threat actors to distribute a peculiar strain of ransomware called “DeroHE” to its forum members. IObit is known for Windows system optimisation and anti-malware programs such as Advanced SystemCare. Members of the forum received an email claiming to be from the company, stating that […]
A cloud misconfiguration by the Chinese social media management company SocialArks exposed 318 million records from Facebook, Instagram, and LinkedIn. More than 400GB of public and private profile data for 214 million social-media users world-wide. The leak stems from a misconfigured ElasticSearch database, which contained Personally Identifiable Information (PII). Researchers discovered that the server was publicly exposed without a […]
An untrusted deserialization vulnerability in the Zend Framework was disclosed this week. If exploited by attackers, they can achieve Remote Code Execution (RCE) on PHP Sites. This vulnerability could impact some instances of the Laminas project, which is Zend’s successor. Zend Framework is built from PHP packages and used by developers to build object-orientated web […]
How the Critical Golang XML parser bug cause SAML authentication bypass? Security researchers at Mattermost, coordinating with the Go security team disclosed three critical vulnerabilities within the Go languages XML parser. If exploited, these vulnerabilities can lead to a complete bypass of Security Assertion Mark-up Language (SAML) authentication, as the vulnerabilities impact Go’s implementation of […]
There are a variety of different ways to assess the security integrity of the systems that process, store, or transmit your information assets. But I find it odd that this far down the cyber security road, a lot of businesses still don’t understand the basic difference between Vulnerability Scanning and Penetration Testing. I know it […]
A Security Engineer at Evolution Gaming has discovered a Cross-site Scripting (XSS) vulnerability on the teams.microsoft.com domain. This could be abused to trigger a Remote Code Execution (RCE) flaw in the Microsoft Teams Desktop Application. According to the researcher, an attacker simply needs to send a specially crafted message to any Teams user or channel […]
A Remote Code Execution vulnerability, in the Oracle WebLogic Server, was recently discovered. The Oracle WebLogic vulnerability was due to the Oracle Fusion Middleware console component, according to Juniper Threat labs, almost 3000 Oracle WebLogic servers are reachable over the internet, based on Shodan statistics. Attackers are targeting potentially vulnerable WebLogic servers using at least […]
ISO 27001 Certification Cost ISO 27001 is an internationally recognised standard for information security management systems (ISMS). It provides a framework for organisations to establish, implement, maintain, and continually improve their information security practices. ISO 27001 outlines clear requirements for managing risks, safeguarding sensitive information, and ensuring data confidentiality, integrity, and availability within an organisation. […]
There was a spike in Phishing and business email compromises due to threat actors exploiting Google services. The attacks weaponize services such as Google Forms, Google docs, and Firebase on mobile to increase the legitimacy from the perspective of security filters and victims. Due to the open nature of the Google ecosystem, attackers are taking advantage […]