As expected, in Q2 this year, cyber criminals shifted their focus to cloud-based apps. A report by Netspoke revealed that 68% of all downloads with malware attached, were dispersed from cloud apps. Now that companies heavily rely on cloud-based services for connectivity and collaboration purposes to support working from home environ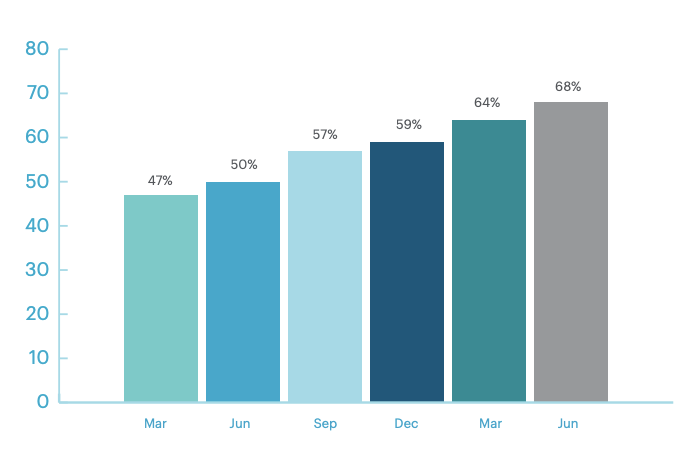 ments – attackers are turning to target the cloud. Why? Read on to find out.
ments – attackers are turning to target the cloud. Why? Read on to find out.
Attacks focus on victim numbers and high-value data
Ransomware threat actors are focusing on multipliers, whether by targeting supply chain attacks or by attacking cloud service providers which allow for easy access to a large number of victims (their account holders) and their data. If there’s one certainty in cyber security, it is that cyber criminals and groups will find and follow where enterprise workers are. Why? Simply put, a larger attack surface = a larger ransom payout.
Organisations don’t just have to worry about attackers asking for a ransom, but additionally, the data may be sold to the cyber market. Bonobos, the men’s clothing store, experienced this earlier in the year. Attackers gained control and downloaded the cloud backup of their database. The threat actor, ShinyHunters, known for hacking cloud services and selling stolen databases, posted the entire database to a free online hacker group.
Whilst the cloud is convenient for organisations, they must be aware of the risks associated with increased cloud usage and its harm to their business. For example, Netskope discovered that 83% of employees access personal app instances on their corporate devices, which greatly increases the likelihood of data being leaked online. This is precisely why popular cloud services that facilitate interaction and simplify companies’ IT infrastructure have become ideal targets.
How malware is being delivered through the cloud
Also, in Q2 2021, it’s notable to mention that 43% of all malware downloads were malicious Office docs, compared to just 20% at the beginning of 2020. This increase came after the world’s most dangerous malware, Emotet, was taken down by law enforcement after a seven-year reign. The increase is likely due to other groups who have learned from Emotet’s success and have implemented similar techniques.
The prime targets being hit
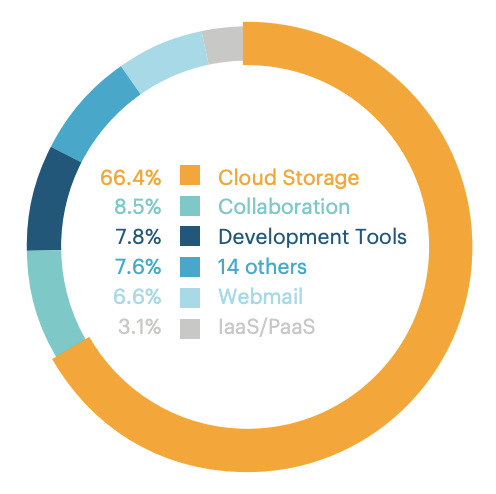
The main target for attackers is firstly cloud storage, collaboration apps, and development tools account for the next largest percentage as attackers abuse popular chat apps and code repositories to deliver malware, according to the Netspoke report
Are any cloud-based services safe?
Most big-name cloud service providers such as Microsoft, Google and Amazon provide a more secure environment than your organisation could maintain with on-site servers. However, as good as cloud providers’ security can be, once your credentials are stolen or when your company data leaves the cloud to interact with other systems – they cannot protect it.
Human actions are what activate breaches. Employees using poor passwords, insecure Wi-Fi connections, and non-awareness of phishing emails is what puts your data at high risk. Therefore, your first defence must be through your people. This is both good and bad news. The good news is that you can create awareness and teach your staff to be safe. The bad news is there is no security software or any person’s smart actions will ever make your organisation 100% secure. So, what can you do now?
How to protect against cloud attacks
Again, good news! There are a few ways you can improve your cloud security. These include (as you may have guessed) staff awareness training, protecting users with multi-factor authentication, managing user access, ensuring on-boarding and off-boarding processes are in place, having a data backup plan, testing for measurements and results.
1. Staff awareness and simulated training
The expansion of Microsoft Office 365 and other collaboration platforms have opened a larger attack surface and hackers are more frequently using phishing emails. Implementing ongoing training, that includes simulated phishing attacks, is a smart way to empower employees to identify these emails before they make the unfortunate click that leads to malware. Simulated phishing attacks can help employees identify these emails before they make the unfortunate click that leads to malware.
Phishing is not all that should be on your radar, but social engineering should be as well. Passwords and other login credentials can be stolen by hackers through smishing, vishing and spoofing.
Regular training will help you not only to measure improvements but set key performance indicators to track your staff awareness goals.
2. Implement multi-factor authentication
Let’s be honest. Traditional usernames and passwords are no longer sufficient to protect against threat actors. Think about it. Would you accept if your online bank account only needed a username and password to access your account?
Adding Multi-Factor Authentication (MFA) is one of the most cost-effective security controls to protect against hackers from accessing your cloud applications. Many security professionals say it’s pure negligence not to have MFA.
3. Manage Your User Access to Improve Cloud Computing Security
Most organisations will already have a policy and process in place to ensure only employees who absolutely need access are authorised to have access. If this is something you do not have in place, you should consider adding this to your security measures.
Let’s consider this scenario, you have an employee who has been given access to everything and he/she receives a phishing email and mistakenly provide their login information to your private cloud. Now the attacker has all access to everything.
There is an alternative if you don’t have the time or IT resources to manage all users’ access. A managed services provider can completely take this task by providing user access and management.
4. Control your on-boarding and off-boarding for both staff and 3rd party suppliers
We all know that when staff leave their access should not leave with them but be removed at their departure. This is easier said than done but facing the consequences of a disgruntled employee stealing or deleting data will be even harder to face. This critical security responsibility often gets pushed back days or weeks after someone has left. Ensure the person leaving can no longer access your cloud storage, systems, data, customer information and intellectual properties before they walk out the door.
It’s important to manage the on-boarding and off-boarding of your cyber suppliers who are connected to your systems and processing your information assets. Your business systems are only as secure as those systems connected to them. Again, if you do not have the internal resources to manage cyber supply chain risk, it can be outsourced to implement and maintain this process.
5. Back up your backup
If you use Microsoft Office 365, then you should note that while backup of your data will be held, it is only within a limited time. This can put you in a bad situation if an employee accidentally deletes files that are vital to your business, and you don’t have a second backup.
It’s good to check with your provider on the period they hold your data and the cost of retrieving it, to then determine the best backup plan for your organisation. Many companies turn to cloud to cloud (C2C) solutions that provide heightened data protection outside what is offered by the SaaS application.
6. Test and retest
You can’t protect what you can’t see. Therefore, it’s vital to conduct penetration security testing to help minimise cloud security threats that are not easily visible. Testing will evaluate your weaknesses and identify vulnerabilities associated with your servers and applications. Before the testing engagement, you should inform your cloud provider as it will simulate a real attack. Once vulnerabilities are found, they will need to be remediated and tested again. When choosing a pen test provider you should see if they include retesting, as some do not or will charge an additional cost.
Start protecting against cloud attacks
Now that you have a few ways to begin a programme to protect your information assets connected to the cloud. Starting doesn’t have to be hard. If you need assistance, the Crew can support your organisation with Cyber Supply Chain Risk Management (C-SCRM) and Cloud Security Testing. Also, we offer a Ransomware Readiness Audit Service that accesses your business’s capability to identify, minimise and manage the risk of a ransomware attack along with cost-effective recommendations for significantly improving your defensive capability.


